Cybersecurity
DNS Security
DNS Security
In general, we use the domain names to specify a website that we intend to visit using Internet.
But in reality, on a technical term, the computer uses an IP Address to identify different systems based on the domain names, those connected to the Internet and route the traffic on it.
The Domain Name System also known as DNS is a protocol that makes the internet usable interpreting the domain value and allows the use of its names.
DNS is a trusted protocol widely used and trusted by enterprise companies, which allows it to freely pass through their Network Firewalls. Cybercriminals usually attacks these DNS systems to steal valuable information from such network and create ruckus.
Under these circumstances DNS is considered a crucial component that requires Network Security.
Cybercriminals uses DNS in various forms of threats that includes attacks against the infrastructure.

Types of DNS Attacks
DDoS – Distributed denial of Service
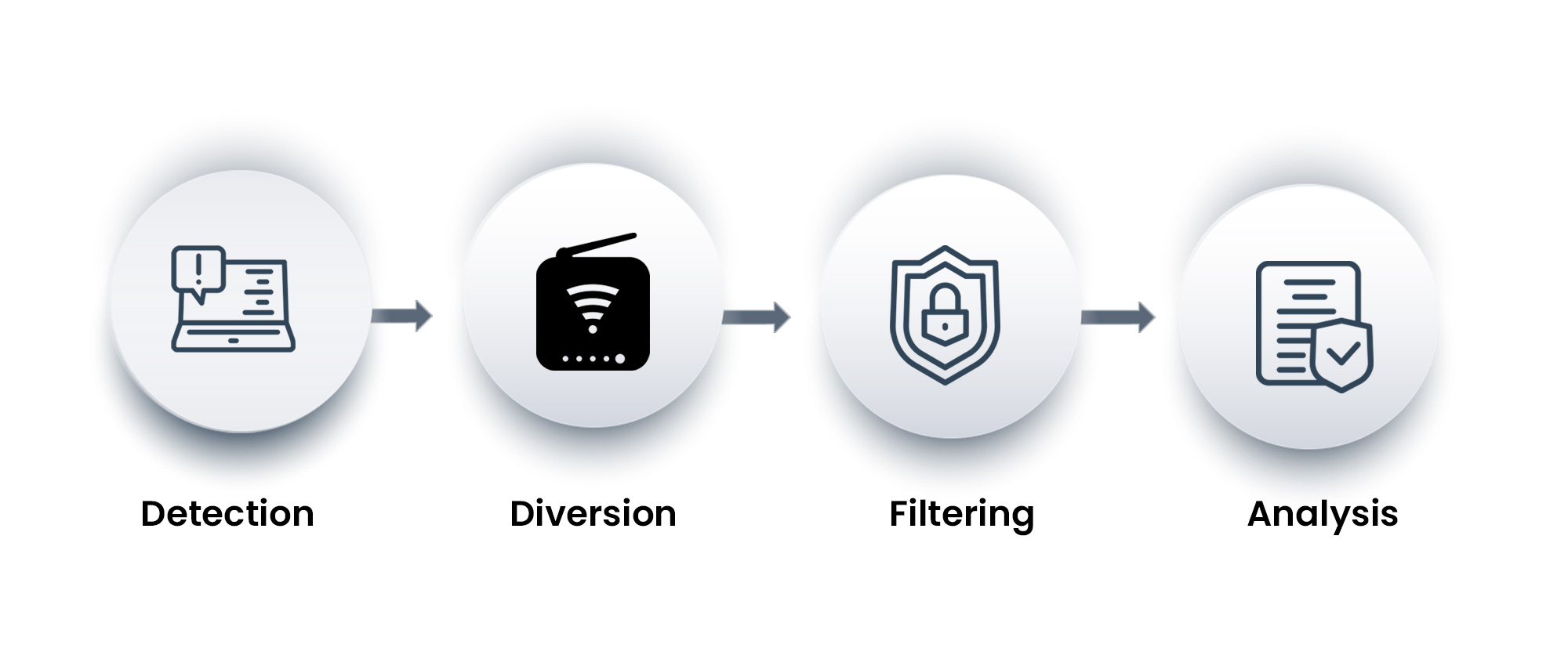
A DDoS is a type of cyberattack on a targeted server, network service, website which floods the DNS with superfluous requests to access with Internet traffic.
Such extreme traffic at Server, Network or services causes the network inoperable.
Smurf Attacks, ICMP Floods, IP/ICMP Fragmentation are some of the DDoS type of cyberattacks.
Cybercriminals attacks using DDoS often, targeting sites or services hosted on high-profile web servers such as banks or credit card payment gateways to exhibit their revenge, blackmailing and demonstrate activism etc.
It is important to note, along with the DNS Networks, even the applications which runs on DNS Servers are badly affected, those targeted by DDoS attacks. Such attacks are programmed to explore the susceptible channels within the applications that make them unable to respond even for legitimate requests.
It is important that a dedicated security is administrated on DNS.
DNS
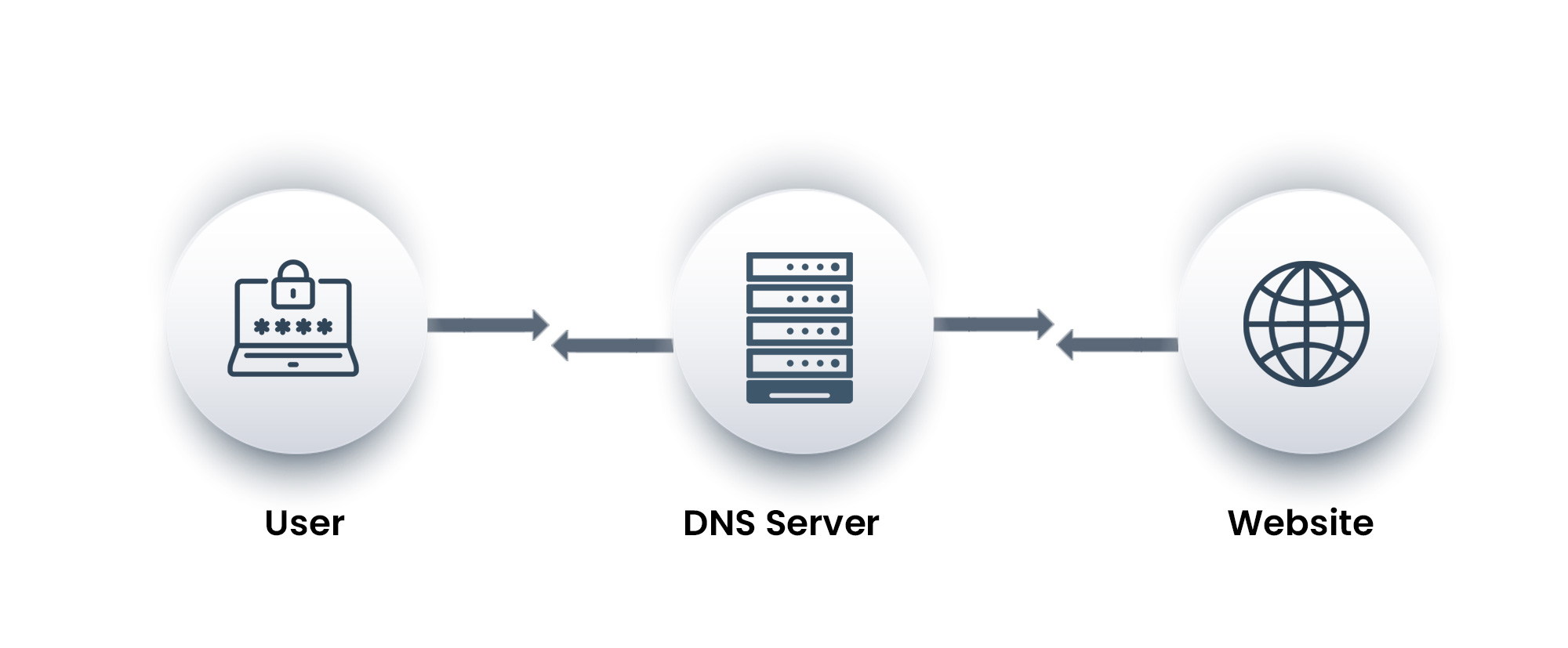
DNS Hi-Jacking and DNS-Tunnelling are the common types of attacks cybercriminals usually do by tricking the user to understand and make them to connect into a legitimate domain. But in reality, they will be connected into a malicious domain. It is in general, that the criminal activity is accomplished using a malicious DNS Server, by storing its incorrect DNS data which is also called as Cache Poisoning.
- Technical, DNS is a trusted protocol that most business networks will access and leave the network without any suspect.
- Cybercriminals take advantage of DNS for data exfiltration along with malware.
- Such exfiltrated DNS requests contains the data being exfiltrated.
Being the Target DNS server controlled by the Owner of the target website, the cybercriminals ensure that the exfiltrated data reaches a server, where it can be processed by them and a response is sent in the DNS response packet causing an illegitimate DNS Tunnelling activity.
How Reich’s programs protect DNS from attacks…?
The Importance of DNS Security
DNS protocol is built with minimal integrated security. Reich Global IT offers solutions to help secure the DNS
With the advent of latest technical resources, RCP (Reich Cybersecurity Program) have successfully adapted and tried in securing the DNS with various solutions backed up by prominent products in this domain.
DNS protections such as Reputation Filtering, DNS Inspection, Securing the Channel are implemented to ensure the DNS is protected in your business network environment.
Logically, the application running on Internet makes the DNS request to find the IP Address of the website to reach out and in the similar way, the malware will make such requests. Reputation filtering is based on the threat intelligence, the proposed security programs implemented at the business IT Infrastructure blocks such unidentified requests and have them redirected thus stopping the users from visiting dangerous sites or executing malware applications communicating at the end point operator.
Another method called DNS Inspection is used to detect and block the “Data Exfiltration” executed via DNS Tunnelling along with malicious activities. DNS Inspection identifies such threats through IPS also known as Intrusion prevention system, which are integrated in to Firewall. Such integrated IPS helps to block DNS attacks through malware command and controls.
One more way to protect DNS is to secure the protocol. DNSSEC is one such protocol that includes authentication for DNS responses. DNSSEC strengthens authentication in DNS using digital signatures based on public key cryptography. With DNSSEC administrated, it is not just the DNS generating queries and provide responses for themselves that are cryptographically signed, but rather, DNS data itself is signed by the owner of the data.
Along with best products and proven solutions, Reich can help organizations protect DNS infrastructure and detect DNS-based attacks. Next-Gen Firewalls detect malicious traffic and DNS tunnelling attacks via Reputation filtering and IPS DNS Tunnelling protections. In addition, we can empower SOC teams to research IoCs and find look alike domains to protect against cyber threats such as those exploiting DNS in phishing attacks.



