Cybersecurity
Cybersecurity
YOUR DATA IS YOUR POWER and IT NEEDS TO BE PROTECTED
Reich IT implements and manages premium cybersecurity solutions for your business.
Associated with best in technology partners and brands, Reich’s Cybersecurity Program helps your business to protect all sorts of sensitive data, personally identifiable information, Health information, Private Data, Intellectual Data, Government and Industrial information systems etc. from Theft and Damage.
Our IS (Information Security) program deals in protecting your business information on cloud, from various types of hacks, such as ransomware, spyware, malware and other types of harmful software that can cause all kinds of havoc.
Reich advances in taking an active role by protecting servers, endpoints, databases and networks by identifying threats and mis-configurations that will always lead to vulnerabilities. Our programs commit to protect preventing such breaches.
Reich prioritizes the cybersecurity program in protecting your business sensitive data.
Our services on Cybersecurity simplifies the security process and addresses all types of threats and assists your business to effectively reach the desired IS protection goals.
Irrespective whether a business needs a custom-built solution for their existing Cybersecurity services or a comprehensive turnkey solution is demanded, Reich’s Cybersecurity program has successfully addressed them all, for both small and medium business and Enterprise companies. Our certified & experienced professional experts will always help you access and manage the security goals of your business.

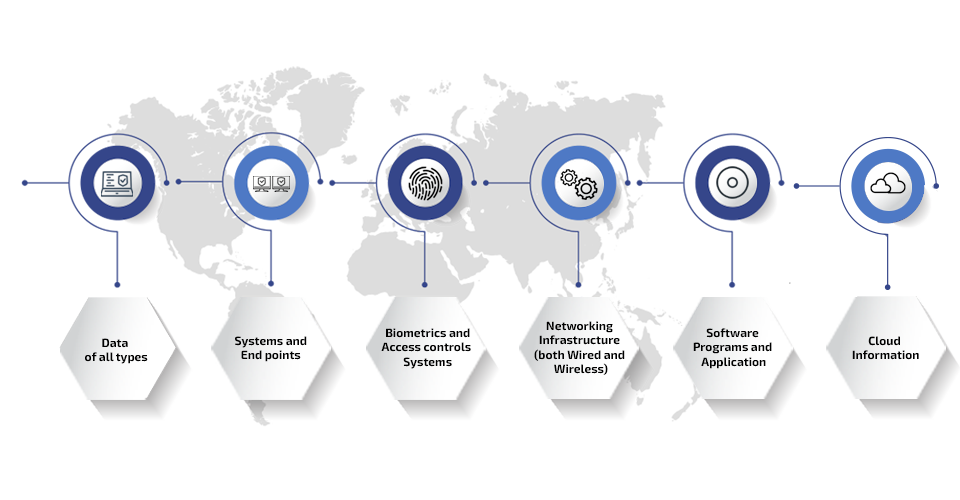
Our Key Cybersecurity
Programs covers protections on
- Data of all types
- Systems and End points
- Biometrics and Access controls Systems
- Networking Infrastructure (both Wired and Wireless)
- Software programs and Application
- Cloud information
The program is bundled involving the complete protection strategy required based on the evaluation of your existing business system and process. Our team creates a plan of execution, which is integrated with managed security services that we offer.
IN SHORT, OUR PROGRAM DELIVERS A BROAD SPECTRUM OF MANAGED CYBERSECURITY SERVICES.
How our Security Programs are Evaluated and Deployed

Understand the
Business Strategy

Evaluate Existing System and Process

Creating a plan of execution with key SLAs

Deploy Security process, integrated with the managed security service offerings
How do we explain & propose the right security strategy to our Clients.
The initial part of our programs help your business to understand the service objectives and aligns the investment on the right security product.
We assist in designing your security program with deep analysis through an industry best security product.
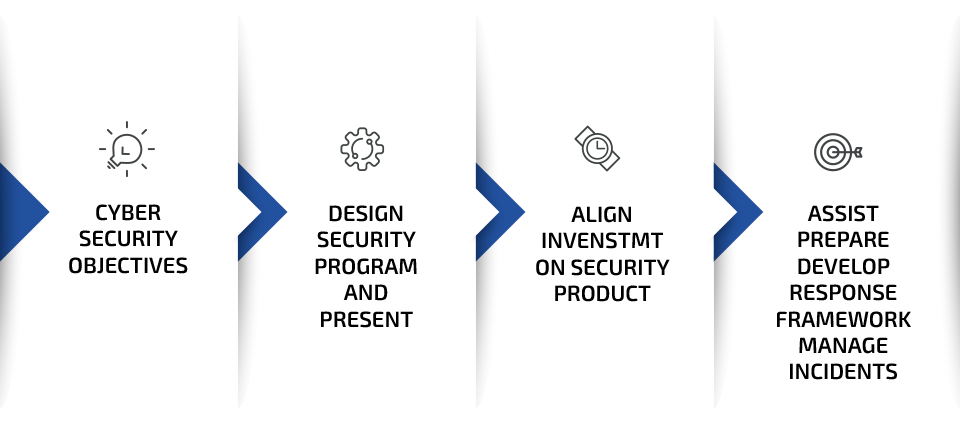
- Objectives of Cybersecurity as a Service
- Design security program and present Detailed Analysis with from Industry best.
- Align the Investment on right security Product.
- Assist in preparation and develop a response framework to cyber Incidents.
Program’s Flexibility
We assist in the preparation and develop a response framework to cyber incidents through one of the best cybersecurity products which extends your business ability to recover and return to normal operation after a cyber-attack.
Deploy and defend
Certified by the team after a complete analysis of the strategy, the outcome offers a detailed transformation based on the plans proposed which leads to a fully functional cybersecurity capabilities, ready for execution.
Few Of The Areas Such Deployment Programs Are Rendered
- Network Firewall and Infrastructure
- Email Applications
- Web based applications
- Database Security
- Data Leak Protection
- Network TAPS & Packet Brokers
- Identity and Access Management
- SIEM & SOAR Deployment
Security Information and Event Management system
Security orchestration, automation and response Deployment - ICS/IOT – Network and Application
- Cloud and Container Security
- Privileged Identity Management
Assess & Assure

Our assessment services help you measure your cybersecurity capabilities skill sets and your readiness to implement stronger defences and more efficient solutions



